Explain Different Types of Hashing Techniques
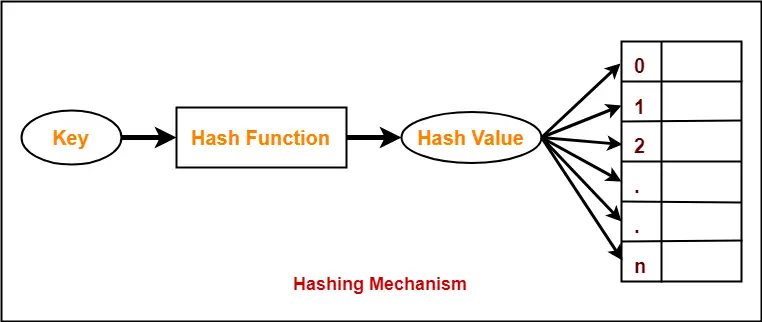
The hash function divides the value k by M and then uses the remainder obtained. The most common methods are open addressing chaining probabilistic hashing perfect hashing and coalesced hashing technique.
Hashing In Cryptography 101 Blockchains
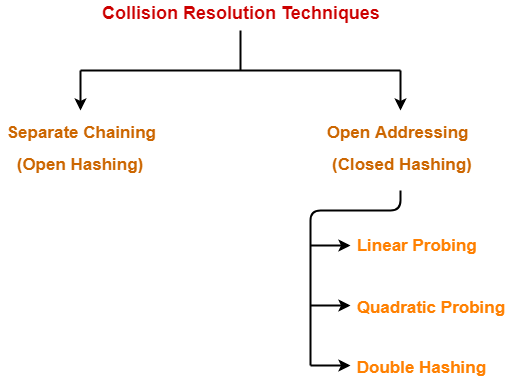
There are two types of collision resolution techniques.

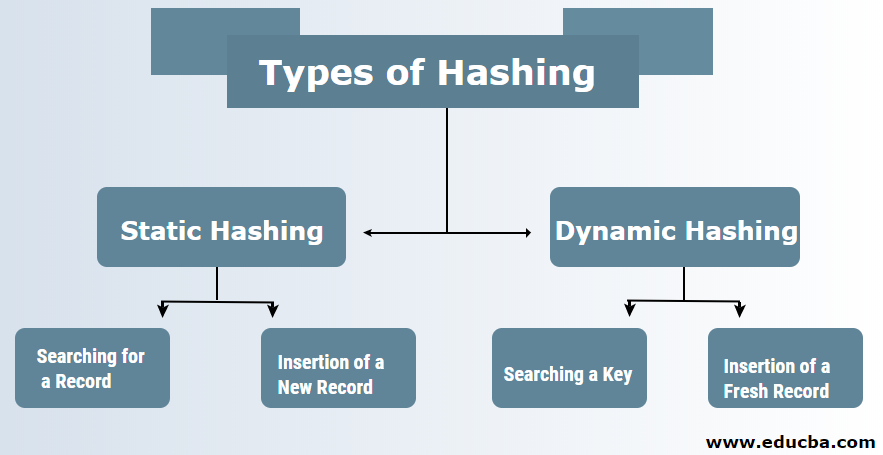
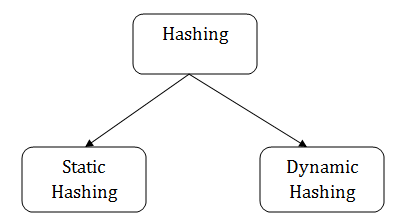
. Two types of hashing methods are 1 static hashing 2 dynamic hashing. 8 78 10. Open Addressing for Collision Handling.
Load Factor and Rehashing. Read the material about Birth Day Paradox in Wikipedia for more info about the possibility of finding a perfect hash and why it is nearly impossible. Elements to be placed in a hash table are 42788964 and lets take table size as 10.
When one or more hash values compete with a single hash table slot collisions occur. Types of a Hash Function In C. Popular Hashing Algorithms Explained Many different types of programs can transform text into a hash and they all work slightly differently.
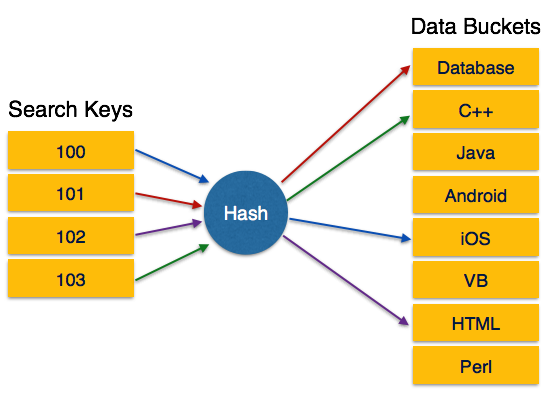
When two or more keys are given the same hash value it is called a collision. Basically a hash is a number that is generated from the text through a hash algorithm. In this case it applies mod 5 hash function on the primary keys and generates 3 3 1 4 and 2 respectively and records are stored in those data block addresses.
Common hashing algorithms include. 9 89 10. Internal Searching Whole data in main memory External Searching Most data.
For example-if the record 52689984 is to be placed in a hash table and let us take the table size is 10. One common method of determining a hash key is the division method of hashing and the formula is. In dynamic hashing a hash table can grow to handle more items.
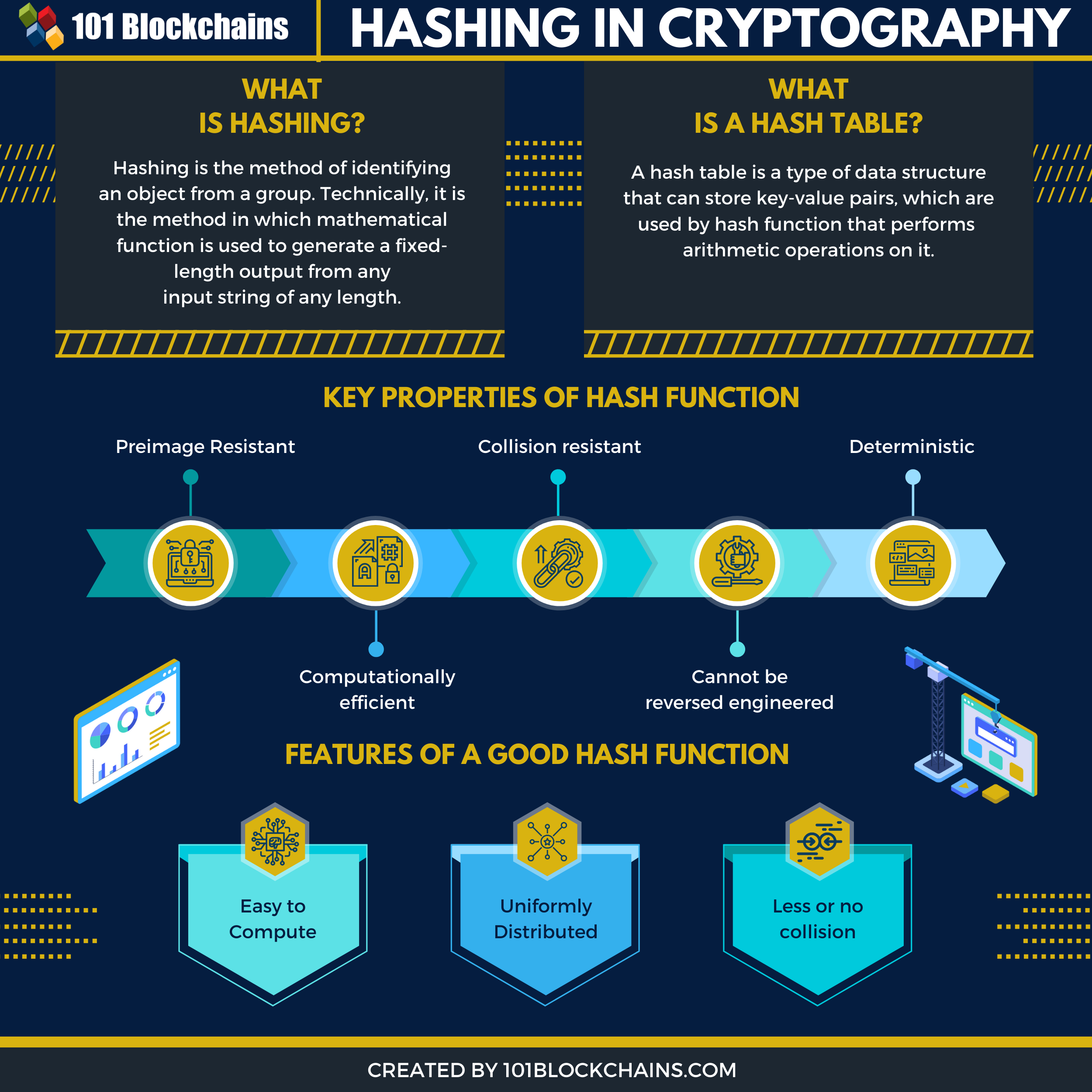
Types of Hashing There are two types of hashing. Lets begin discussing these methods in detail. Cryptography deals with various security principles which are as follows.
MD5 - An MD5 hash function encodes a string of information and encodes it into a 128-bit fingerprint. In this the hash function is dependent upon the remainder of a division. Hash collision resolution techniques.
There are many different types of hash algorithms such as RipeMD Tiger xxhash and more but the most common type of hashing used for file integrity checks are MD5 SHA-2 and CRC32. The types of hash functions are explained below. This is one of the first algorithms to gain widespread approval.
In the static hashing the resultant data bucket address will always remain the same. In static hashing the hash function maps search-key values to a fixed set of locations. Introduction Process of finding an element within the list of elements in order or randomly.
Types of hash function. 2 42 10. To resolve this the next available empty slot is assigned to the current hash value.
Index Mapping or Trivial Hashing Separate Chaining for Collision Handling. Division method or reminder method takes an item and divides it by the table size and returns the remainder as its hash value. MD5 is often used as a checksum to verify data integrity.
A table of records in which a key is used for retriev al is often called a SEARCH TABLE or DICTIONARY. In our example when we add India to the dataset it is appended to the linked list stored at the index 5 then our table would look like this. This article focuses on discussing different hash functions.
The algorithm is designed in such a way that no two hashes are the same for two different texts. Hashing Technique In Data Structures. Caesar cipher monoalphabetic cipher homophonic substitution cipher Polyalphabetic Cipher Playfair cipher rail fence One-time pad hill cipher are some of the examples of cryptography techniques.
Hash key Elements table size. There are various types of hash function which are used to place the data in a hash table 1. It was designed in 1991 and at the time it was considered remarkably secure.
This number is smaller than the original text. Data bucket Key Hash function Linear Probing Quadratic probing Hash index Double Hashing Bucket Overflow are important terminologies used in hashing. This is the most simple and easiest method to generate a hash value.
In this method the hash function is dependent upon the remainder of a division. Separate chaining open hashing Open addressing closed hashing Separate chaining. Hash Key Key Value Number of Slots in the Table.
To handle this collision we use collision resolution techniques. The associated hash function must change as the table grows. Rather the data at the key index.
Hash collision handling by separate chaining uses an additional data structure preferrably linked list for dynamic allocation into buckets. Open Hashing Separate chaining Open Hashing is a technique in which the data is not directly stored at the hash key index k of the Hash table.
Hashing Techniques In Data Structure Pdf Gate Vidyalay

Hashing Algorithm Overview Types Methodologies Usage Okta

Hashing Techniques Interviewbit
Hashing In Data Structure Hash Functions Gate Vidyalay

Hashing Techniques Ppt Download
Hashing In Dbms 2 Main Types Of Hashing Techniques In Dbms

What Is Cryptographic Hashing Md5 Sha And More Tiptopsecurity
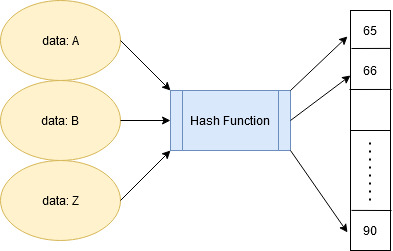
Different Collision Resolution Techniques In Hashing
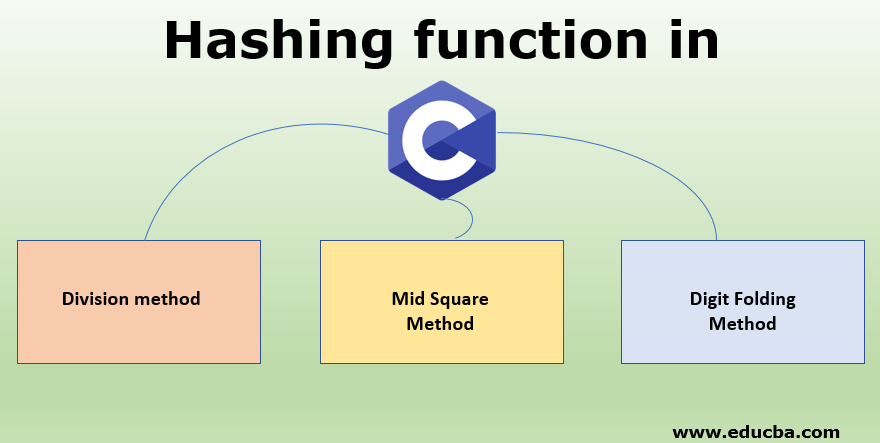
Hashing Function In C Types Of Collision Resolution Techniques

Extendible Hashing Dynamic Approach To Dbms Geeksforgeeks

Hashing Algorithm The Complete Guide To Understand
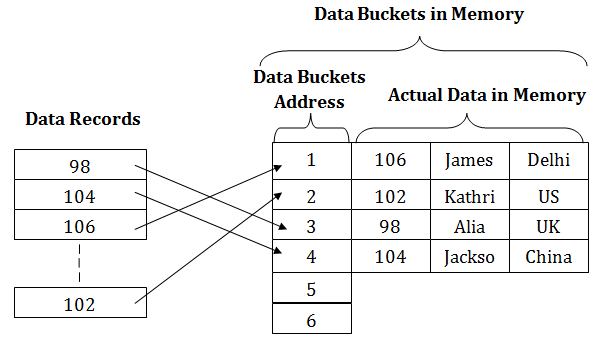
Dbms Static Hashing Javatpoint
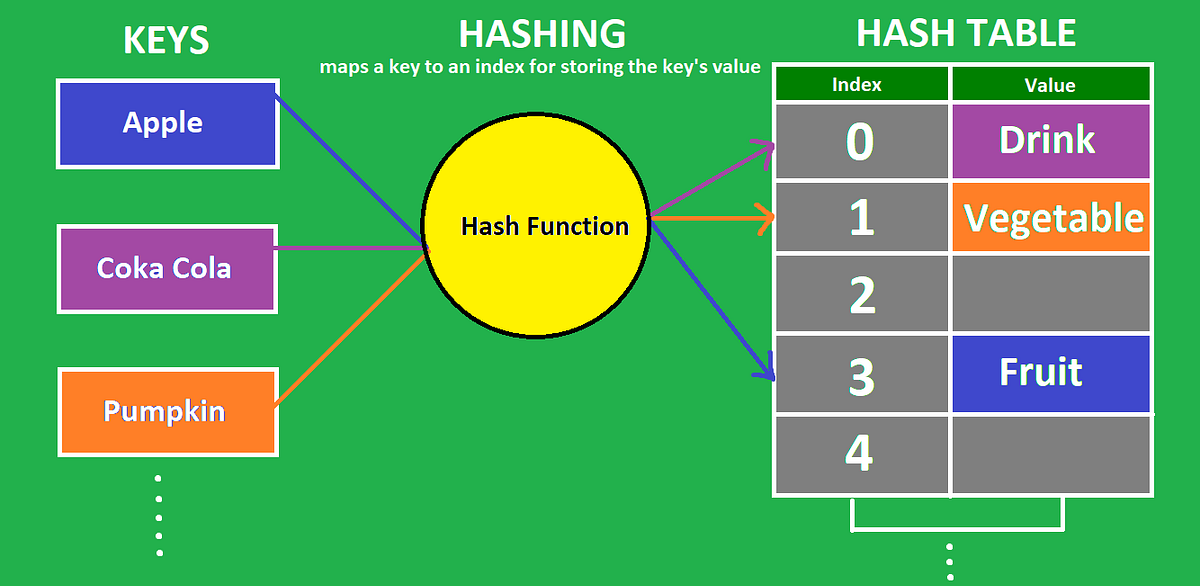
Hash Tables Hashing And Collision Handling By Tawhid Shahrior Codex Medium

Hashing Techniques Interviewbit

Hashing In Dbms 2 Main Types Of Hashing Techniques In Dbms

Comments
Post a Comment